- Written by: vinay
- March 26, 2025
- Categories: AI for Cybersecurity
- Tags:
24/7 Digital Guardians: How Automated Security Is Transforming Data Protection
In today’s fast-paced digital landscape, data has evolved into something far more significant than mere numbers; it has become an integral part of our identities. This document explores the fascinating world of automated security monitoring, which acts as a vigilant guardian over our most valuable digital assets. With a team of invisible protectors constantly on watch, this innovative technology is revolutionizing the way we secure our online lives.
Unveiling the Dimensions of Automated Security

The Digital Danger Zone: The Importance of Constant Vigilance
Every second, new threats emerge from every direction. Cybercriminals, malicious software, and sophisticated ransomware are constantly adapting their strategies. Relying on traditional security measures is akin to using outdated defenses in a world where agility and speed are paramount. Enter automated security systems—equipped with artificial intelligence and machine learning—that function like modern-day knights, swiftly identifying and neutralizing threats in the blink of an eye.
How the Digital Watchdogs Work
Every second, new threats emerge from every direction. Cybercriminals, malicious software, and sophisticated ransomware are constantly adapting their strategies. Relying on traditional security measures is akin to using outdated defenses in a world where agility and speed are paramount. Enter automated security systems—equipped with artificial intelligence and machine learning—that function like modern-day knights, swiftly identifying and neutralizing threats in the blink of an eye.
Imagine having a dedicated team of experts who never need to rest. This is the essence of
automated security monitoring. These digital sentinels utilize advanced algorithms to:
• Monitor network traffic and log files around the clock,
• Identify unusual activities or patterns that raise red flags,
• Send immediate alerts when something seems amiss,
• Automatically intervene to mitigate potential breaches,
• Continuously learn and adapt as new threats emerge.
Automated Security Monitoring Cycle
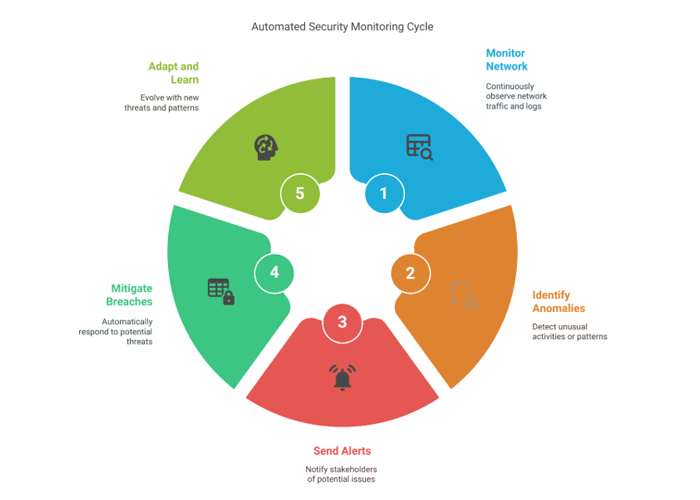
This capability allows them to sift through vast amounts of data almost instantaneously—something no human team could realistically achieve.
Humans and Technology: A Unique Collaboration
While these systems may seem almost magical, their purpose is not to replace human expertise but to enhance it. Automated tools empower security professionals to focus on strategic planning and high-level decision-making, rather than getting bogged down in endless alerts and data. Consider this: while a human team might take hours or even days to detect a subtle breach, an automated system can respond almost instantaneously, potentially saving organizations from significant financial losses and damage.
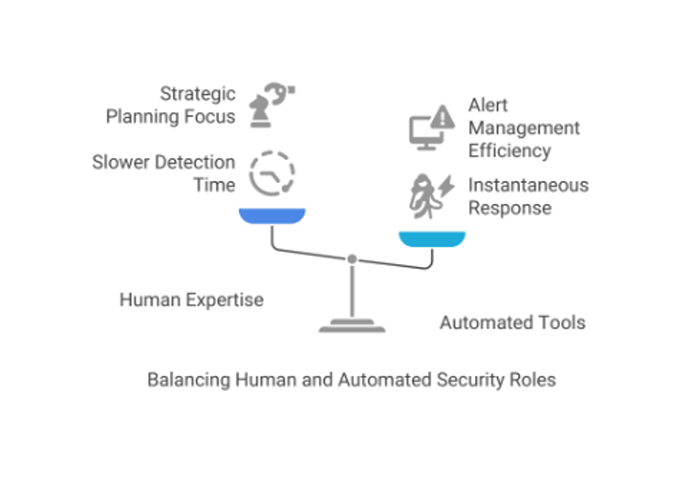
Real-World Success Stories
Across various industries, businesses are already experiencing the advantages of automated security. For example, banks have reported a nearly 70% reduction in response times, and hospitals are now able to protect patient information more effectively than ever. Even smaller businesses and freelancers can access top-tier security solutions without breaking the bank. If you’re interested in exploring these cutting-edge options, there are numerous recommendations available that could transform your approach to digital security.
Looking Ahead: Anticipating Issues Before They Arise
The future of automated monitoring is not just about reacting to threats; it’s about anticipating them. By analyzing historical data and trends, these systems can predict where vulnerabilities may arise. Imagine a security framework that not only prepares for attacks but actively builds protective barriers around your assets. This proactive approach is shifting the focus of cybersecurity from reactive measures to strategic foresight.
The Technology Behind the Transformation
Several groundbreaking technologies are driving this revolution, including:
• Advanced artificial intelligence that continues to evolve,
• Learning algorithms that adapt over time,
• In-depth analysis of behavioral patterns,
• Secure cloud-based infrastructures,
• Early developments in quantum computing capabilities.
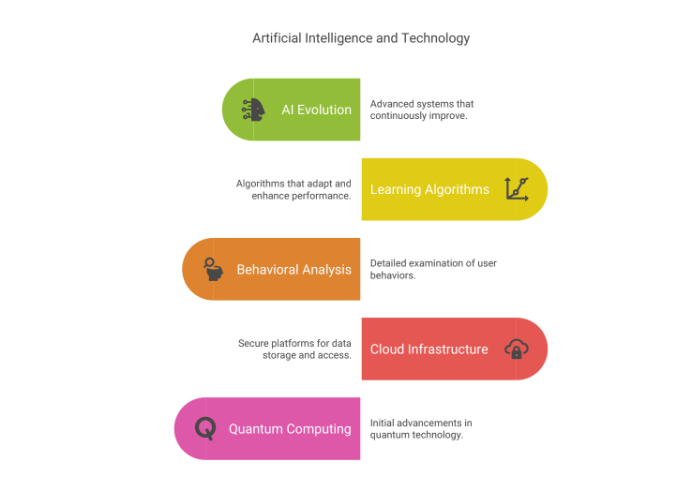
These elements work together to enhance our defenses, making them more adaptable and far-reaching.
Security for Everyone: Making Advanced Protection Accessible
One of the most encouraging aspects of this technological evolution is its increasing accessibility. What was once the domain of large corporations is now available to businesses of all sizes—and even individuals. In a world where our digital lives are both fragile and essential, having robust security measures is no longer a luxury; it’s a necessity. Access to advanced security tools is now within reach for everyone, from large enterprises to solo entrepreneurs. This democratization of technology means that regardless of your technical expertise or budget, you can safeguard your digital assets.
While automated systems are powerful, the human element remains crucial. These systems are not infallible, and it’s essential to stay informed about emerging online threats and maintain basic digital hygiene. Think of it as a combination of high-tech tools and traditional vigilance. Here are some key practices to follow:
• Regularly update your systems.
• Use strong, unique passwords.
• Be cautious of suspicious emails and phishing attempts.
• Understand how your security tools function.
Around-the-clock monitoring is more than just a technological upgrade; it’s a fundamental shift in our approach to digital safety. These relentless digital guardians are not only protecting our data but also preserving our online freedom, fostering innovation, and providing peace of mind in an increasingly complex world.
As we look to the future, the lines between human insight and machine intelligence will continue to blur, creating a safer and more interconnected global landscape. The focus will shift from building higher walls to developing defenses that are both intelligent and adaptable.
So, are you ready to embrace this new era of digital protection?


